T5 Access Control Management Crack For Windows
The T5 access control software is a great tool for controlling and protecting restricted areas or areas where important information or valuable merchandise is stored. This software works with finger print access control systems as well as RFID, and MIFARE readers.
Different access privileges can be assigned to each user and reports can be easily exported to an excel spread sheet or as a text file. Get T5 access control management and take it for a spin to see what it can actually do for you!

T5 Access Control Management (LifeTime) Activation Code [Mac/Win] (2022)
T5 Access Control Software is the only software available to stop people attempting to gain access to areas that are either blocked or locked, by requiring entry of a secret code (or token) and a fingerprint. T5 is powerful, reliable and fully cross compatible with any existing system. The T5 Software and hardware acts as an Access Control Kiosk (ACK) which requires a fingerprint and a secret code that the user is registered with. The T5 access control software is designed to be used for both commercial and residential applications. Access Control Access Control is the process of establishing or verifying access rights to a specific area. There are various types of access control devices, including magnetic card readers and keypads. Fingerprint access control devices are used to restrict access based on identification of the owner or previous transaction with the device. Fingerprint access control devices require a fingerprint identification of the individual (user) and are normally used in a secure or restricted area. As one of the most popular types of access control devices, fingerprint access control is usually available in a wide variety of configurations to fit the exact requirements of a particular application. Existing systems: An existing access control system is one where the access rights of a user or group of users have been previously established. The existing system can use magnetic cards, card readers, manual or electronic keypads to control access. It is common for many existing systems to include an access code which must be provided by the user. Where the keypad is a mechanical push button type, it is common for the access code to be displayed on a display screen when the device is activated. Fingerprint access control: A fingerprint access control system is one which is designed to identify a user or group of users based on a fingerprint. In this type of access control system, a user swipes their finger against the device, and a fingerprint scanner reads a unique pattern, such as a fingerprint, from the surface of the skin. The scan is then compared to a database of fingerprints which will be compared to the fingerprint of the individual or individuals attempting access. A match is normally considered to be a positive identification of the owner of the fingerprint. The individual or individuals who are not the owner of the fingerprint are then rejected and access is denied. Automatic fingerprint identification: Fingerprint access control systems also include a fingerprint scanner which is capable of capturing a fingerprint image and comparing the image to a database of fingerprints. The fingerprint information of the individual is compared to the information held in the database and the result is a positive or negative identification of the
T5 Access Control Management [Updated] 2022
?
Feature:
T5 access control software is a great tool for controlling and protecting restricted areas or areas where important information or valuable merchandise is stored. This software works with finger print access control systems as well as RFID, and MIFARE readers.
Different access privileges can be assigned to each user and reports can be easily exported to an excel spread sheet or as a text file. Get T5 access control management Crack Free Download and take it for a spin to see what it can actually do for you!
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete and rename all of the tables in a database application, work with forms, macros, functions, subroutines and procedures and automatically populate data based on criteria selected from one or more tables.
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete and rename all of the tables in a database application, work with forms, macros, functions, subroutines and procedures and automatically populate data based on criteria selected from one or more tables.
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete and rename all of the tables in a database application, work with forms, macros, functions, subroutines and procedures and automatically populate data based on criteria selected from one or more tables.
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete and rename all of the tables in a database application, work with forms, macros, functions, subroutines and procedures and automatically populate data based on criteria selected from one or more tables.
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete and rename all of the tables in a database application, work with forms, macros, functions, subroutines and procedures and automatically populate data based on criteria selected from one or more tables.
Client Suite Description:
This software is a server solution for managing all aspects of a Microsoft Access database application. The software includes the following features: add, edit, delete
a86638bb04
T5 Access Control Management Crack + Download
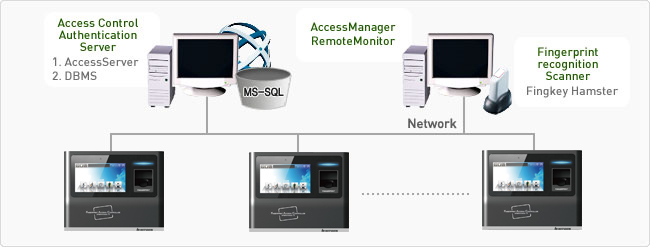
The T5 Access Control System is one of the most advanced Access Control Systems that can be installed using a phone line and is compatible with all T5 Finger Print Readers or any DCT100/500/600/700 RFID card reader. T5 Security Systems is the only manufacturer of PCD (Pass Card Devices) that provides you with a lifetime warranty, 5 year back support, and low cost that is still very high quality.
The T5 system is designed to work with the most popular pin code readers on the market today such as the DCT100, DCT500, DCT600, and DCT700. These Finger Print Card Readers include a low cost, high quality, easy to use, and user friendly interface. The T5 Access Control System has been designed so that even users with minimal computer experience can easily use it.
The T5 Access Control System is also very easy to integrate into any existing PCD and PIN system. T5 security systems also have the ability to make use of up to 200 individual access cards or electronic keys to control access. By default, the T5 Access Control System allows you to assign each user a user name and password. This can be changed if desired and can be changed at any time.
All the database records that you create can be stored in a text file or in a database such as MS-Access, MySQL or Oracle. The T5 Access Control System can be installed on any Windows PC in just a few minutes.
The T5 Access Control System also works with each T5 Card Reader including the DCT100, DCT500, DCT600, and DCT700. All of the interface screens will display when the correct fingerprint or smart card is inserted in the reader. Once the correct fingerprint or smart card is inserted, you will be prompted to enter a username and password. This information will be written to the memory of the card reader and will be retrieved when the card is subsequently scanned.
If a card or fingerprint is not recognized, the system will ask the user to enter the correct username and password. Once the user successfully enters the correct username and password, the system will be able to identify the card or fingerprint and give full access to that individual. If the user enters an incorrect password or card, the system will ask for the correct username and password and the process will begin again.
T5 Access Control System
With the T5 Access Control System, you can protect your data files and data
What’s New In?
T5 Access Control Software is an ideal access control system for security and protection of restricted areas. It works with readers such as RFID, Mifare, and fingerprint sensors to secure and protect the buildings you need. With this software you can easily set up zones, administer access rights to each user, and manage access history. T5 is easy to use, powerful, and affordable.
Get T5 Access Control Software and take it for a spin to see what it can actually do for you.
Product Features:
The fingerprint reader in T5 access control software can be used to grant access to rooms in your facility and to use wireless technology to control access.
T5 software works with any fingerprint reader. And the front screen shows your attendance history and your access rights. You can set up multiple fingerprint readers with T5.
T5 software is an ideal access control solution for security and protection of restricted areas.
Easy to use:
1) Drag and drop your fingerprint image into T5.
2) Activate a zone, and create users.
3) Set up your attendance history and access privileges.
4) Assign access rights to each user.
5) Export your access rights, attendance history, and access privileges to an excel spread sheet.
6) Export your attendance history and access rights to a text file.
7) Delete a zone, user, or access privilege.
8) With T5 software you can easily set up zones, administer access rights to each user, and manage access history.
The Attendance History Screen:
1) You can easily view your attendance history by using the monitor window.
2) To add or delete a user or access privilege, click the plus/minus button in the bottom right corner.
3) To print your attendance history, click the print button.
Security/Protection:
1) The zone you assign to each user will allow or disallow access to the room it is assigned to.
2) You can choose between 1 to 10 users that will have access to the room.
3) If you have more than 1 fingerprint reader, you can assign different fingerprint images to different readers.
4) All users will be displayed in the attendance history screen.
5) You can delete a user, and a user that does not have access to a zone, and the zone will be removed from the attendance history.
6) You can remove a zone, and the assigned fingerprint images will be deleted.
7) All attendance history information is automatically saved to the T5 database.
8) You can export your attendance history as a text file, which can be used as a template for your own personal information tracking software.
9) After the installation, you can use the ‘Check’ option to scan your fingerprint image, if you have one.
10) All access privileges that have been used will be displayed in the attendance history.
https://new.c.mi.com/global/post/486935/HACK_GameDownload_PUBG_MOBILE_100103_105727123exe_
https://magic.ly/puruFquire/Call-Of-Duty-Modern-Warfare-2-Multiplayer-Crack-Hack-Offline-orVERIFIEDor
https://new.c.mi.com/global/post/492137/TommyTronicdownloadlaptop_EXCLUSIVE
https://new.c.mi.com/th/post/1367167/Torrent_Download_Fusion_Connect_2019_Download_BEST
https://new.c.mi.com/ng/post/75458/ANSYSPRODUCTS160WINX64-SSQ_NEW_Full_Version
https://new.c.mi.com/ng/post/73767/UltraISO_Premium_Edition_V8511860_Registered_Multi
https://new.c.mi.com/th/post/1366255/Solucionariodetermodinamicavanwylen2edicionzip
https://new.c.mi.com/th/post/1366260/Descarga_Gratis_Comic_Eroticos_Ruta_69_NEW
https://new.c.mi.com/th/post/1362089/Annabelle_2014_Extras_1080p_BluRay_X264_Dual_Audio
https://new.c.mi.com/my/post/465842/Transoft_Solutions_Nexus_Download_Crack_2021
https://new.c.mi.com/my/post/466451/Every_Child_Is_Special_Movie_Download_UPDATED_Utor
https://new.c.mi.com/th/post/1362064/Toontrack_EZdrummer_EZX_Metalheads_HYBRID-4sharedt
https://new.c.mi.com/th/post/1367798/Mflare_2_Free_Fix_Download_For_Mac
https://magic.ly/puruFquire/Rld.dll-Lego-Harry-Potter-Crack.rar-!!BETTER!!
https://magic.ly/0mensplicWchronke/Double-Dhamaal-Full-Movie-Download-In-Hindi-720p-Extra-Quality
https://magic.ly/perrecntupya/Extra-Quality-Cheque-Express-Lite-V5.5-orBESTor-Full-Version-Download
https://magic.ly/1frunurjunczo/Free-Online-Minecraft-Gift-Code-Generator-No-((BETTER))-Download-No-Survey
https://new.c.mi.com/global/post/490959/Ps3_Emulatorx_V117_Bios_CRACKED_Free_12
https://new.c.mi.com/ng/post/75453/Use_Amiquote___EXCLUSIVE___Cracked_Amibroker_Downl
https://new.c.mi.com/global/post/492132/Universal_Maps_Downloader_937_Keygen_PORTABLE_Crac
https://new.c.mi.com/ng/post/75329/Black_Monkey_Pro_Sleepover_Guide_Pdf_FREE
https://new.c.mi.com/my/post/466446/The_Standard_Book_Of_Spells_Grade_2_By_Miranda_Gos
https://new.c.mi.com/my/post/466441/Solution_Manual_For_Bioseparations_Science_And_Eng
https://new.c.mi.com/ng/post/75085/Diskinternals_Vmfs_Recovery_21_Keygen_11_2021
https://new.c.mi.com/my/post/466436/HD_Online_Player_Navra_Mazha_Navsacha_Full_Movie_H
https://new.c.mi.com/my/post/466431/Passware_Filemaker_Password_Recovery_Key_6378535
https://new.c.mi.com/global/post/492127/Memento_Firmware_13
https://new.c.mi.com/global/post/489066/Atomic_Alarm_Clock_60_Serial_Number
https://new.c.mi.com/my/post/466421/AutoCAD_Map_3D_2019_64bit_Keygen_Xforce_PATCHED
https://new.c.mi.com/my/post/464500/CCleaner_Pro_5637540_Crack_License_Key_Latest_Vers
https://new.c.mi.com/ng/post/75075/X_Force_2012_X32_Exe_Autodesk_Rendering_FULL
https://new.c.mi.com/global/post/492122/Gta_Vice_City_2010_Free_Download_Utorrent_My_Pc_RE
https://new.c.mi.com/my/post/464299/Download_Aurora_3d_Presentation_BETTER_Full_Versio
https://new.c.mi.com/my/post/465837/Xforce_LINK_Keygen_Robot_Structural_Analysis_Profe
https://new.c.mi.com/my/post/464490/Tablebuilder_For_Autocad_Crack_13l_BETTER
https://new.c.mi.com/ng/post/75443/FSX_-_Eaglesoft_Cirrus_SR22_Turbo_Torrent_Extra_Qu
https://new.c.mi.com/global/post/490954/X_Force_Keygen_Shotgun_2018_Free_Download___TOP
https://new.c.mi.com/ng/post/75438/Free_Download_Bud_Redhead_Setup_Full_Version__TOP
https://new.c.mi.com/my/post/466416/InPixio_Photo_Focus_355905_Multilingual_Incl_Keys_
https://new.c.mi.com/my/post/464294/Balak_Palak_Marathi_Movie_Download_TOP_720p_Torren
https://new.c.mi.com/my/post/464485/Us_Pharmacopoeia_Free_HOT_Download_Pdf
https://new.c.mi.com/th/post/1366110/Estate_Bruno_Martino_Guitar_Pdf_Download_VERIFIED
https://new.c.mi.com/ng/post/75070/HD_Online_Player_dabangg_2010_Hindi_Brrip_720p_NEW
https://new.c.mi.com/my/post/464284/Ek_-_The_Power_Of_One_Movie_720p_Free_Download__TO
https://new.c.mi.com/ng/post/75433/Igo_Primo_800400_Autoradio_Noname_Gps
https://new.c.mi.com/ng/post/75324/Ezdrummer_Vsti_Drumkit_From_Hell_Torrent_TOP
https://new.c.mi.com/th/post/1366085/Windows_7_8_102_12_Loader_Activator_V9013_Reloaded
https://new.c.mi.com/global/post/492117/Microsoft_Office_Professional_Plus_2010_Setup_Acti
https://new.c.mi.com/ng/post/75065/Gta_5_Wallpapers_Download_NEWl
https://new.c.mi.com/ng/post/73621/Batman__Arkham_Knight_-_Season_Of_Infamy_Most_Want
https://magic.ly/puruFquire/Forgiveness-:-Escape-Room-Free-Download-PATCHED-FULL
https://new.c.mi.com/ng/post/73762/Auto_Macro_Recorder_Pro_52_Crack_UPDATED
https://new.c.mi.com/my/post/465822/Medal_Of_Honor_2010_No_Cd_Crack_Download_TOP
https://magic.ly/sanaesyngmo/Entrenamientoavanzadotudorbompapdfdownload-((BETTER))
https://new.c.mi.com/ng/post/75060/Radmin_34_Serial_Number_42_BEST
https://magic.ly/icnisQofga
https://new.c.mi.com/ng/post/75319/Refx_Nexus_241_Installer_Rar_Password
System Requirements For T5 Access Control Management:
Minimum System Requirements:
• AMD, NVIDIA or Intel graphics card
• Display: 1024 x 768, Windows 7/8
• Processor: Core i3-540, 2.13 GHz
• RAM: 4 GB (8 GB recommended)
• Hard Disk: 40 GB available space
• DirectX: 9.0c
• OS: Windows 7/8
Recommended System Requirements:
• Display: 1280 x 1024, Windows 7/8
• Processor: Core
https://www.scoutgambia.org/multiply-in-your-head-crack-mac-win-2022/
http://shop.chatredanesh.ir/?p=177403
http://www.interprys.it/history-search-for-chrome-crack-keygen-for-lifetime-download-win-mac.html
https://discovery.info/proxycommander-crack/
http://steamworksedmonton.com/area-code-lookup-crack-torrent-activation-code/
https://kitchenwaresreview.com/web-link-builder-crack-activation-free-download/
https://klassenispil.dk/esbackup-crack-free-3264bit/
ใส่ความเห็น